Introduction to IGA
Identity Governance and Administration (IGA) refers to a set of processes and policies designed to manage digital identities and their associated access rights throughout the entire lifecycle. The central theme of IGA is to prioritize security, compliance, and operational efficiency, providing organizations with a dynamic framework suitable for the complexities faced in today’s digital landscape.
In the context of modern organizations, where digital identities are frequently created, modified, and deprovisioned, IGA ensures that access management is closely aligned with business needs and regulatory requirements. The IGA framework makes it possible to manage user access effectively while also ensuring that sensitive data is protected against unauthorized access and breaches.
IGA solutions are adaptable and designed to meet the varying needs of contemporary businesses, integrating seamlessly with existing systems and policies. By leveraging automation and advanced tools, IGA helps organizations streamline identity lifecycle management processes such as provisioning, access changes, and deprovisioning.
Additionally, IGA places a strong emphasis on governance, ensuring that access to resources is granted based on defined criteria and that only authorized parties can make access decisions. This governance structure helps mitigate risks associated with identity theft, data breaches, and regulatory non-compliance.
In this training document, we will explore the core components of IGA in detail, including identity lifecycle management, access management and governance, the principles of single sign-on and federation, compliance considerations, roles-based access control, and privileged access management. By understanding these concepts, organizations can implement effective identity governance strategies that enhance security, improve operational efficiency, and maintain compliance with industry regulations.
Identity Lifecycle Management in IGA
Identity Lifecycle Management is a cornerstone of Identity Governance and Administration (IGA) and is essential for effectively managing digital identities within an organization. This component encompasses a series of processes that span the entire lifecycle of an identity, from creation to deletion. Below is a detailed breakdown of these processes:
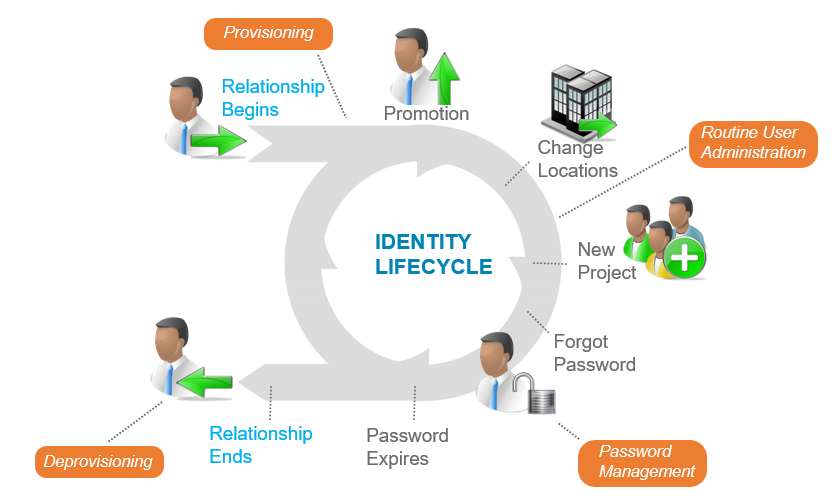
Provisioning
Provisioning is the process of creating and assigning digital identities as soon as an individual joins the organization. This is typically automated using tools such as Empower ID, which streamlines the user onboarding experience by automatically creating user accounts and assigning roles and permissions suitable for the new employee's position.
- Example: When a new employee is hired, the provisioning process kicks in where their digital identity is established in the system, which includes the setup of email accounts, access to necessary tools, and assignment of default roles that dictate their access privileges.
Access Changes
As employees progress through their careers, their access needs will change due to various factors such as promotions, relocations, or shifts in job responsibilities. Managing these access changes is critical to ensuring that users maintain appropriate access levels.
- Dynamic Adjustments: Employees might be assigned additional access rights due to new job roles or responsibilities. This could also mean they need to lose access to certain resources that are no longer relevant to their updated role.
- Continuous Monitoring: Organizations must continuously monitor these changes to ensure access remains aligned with the current job function.
Password Management
Throughout their lifecycle, digital identities require regular updates and maintenance of credentials, such as passwords. This includes managing password expiration, resets, and updates.
- Password Expiration: Regular password changes are crucial for security. Users may be prompted to change their passwords periodically to minimize the risk of unauthorized access.
- User Self-Service: Many organizations implement self-service capabilities to allow users to reset their passwords, reducing the administrative burden on IT.
Deprovisioning
Deprovisioning occurs when an individual leaves the organization. This is a critical step to ensure that access rights are promptly revoked upon termination.
- Immediate Action: It’s essential for security that the deprovisioning process is immediate to prevent former employees from retaining access to sensitive information and resources.
- Lifecycle Management: Effective lifecycle management ensures that all access is revoked systematically, which includes disabling accounts and removing roles and permissions associated with the departed individual.
Importance of Lifecycle Management
The comprehensive management of identity lifecycles ensures that organizations can maintain security, compliance, and operational efficiency. By implementing automated processes for provisioning, access changes, password management, and deprovisioning, organizations can significantly reduce the risk of security breaches and maintain oversight of user access rights throughout the individual’s employment.
In summary, identity lifecycle management is an essential component of IGA that requires diligent planning and execution. It lays the groundwork for effective access management and governance, helping to streamline operations and enhance security compliance as users transition throughout their careers in an organization.
Access Management and Governance in IGA
Access management and governance are vital components of Identity Governance and Administration (IGA), ensuring that users have the appropriate permissions to perform their tasks while maintaining organizational security standards. This section delves into the intricacies of these concepts, discussing how they operate within an IGA framework.
Access Management
Access management focuses on controlling user access to various systems and applications to ensure that only authorized users can perform specific actions.
Key Aspects of Access Management:
- Authorization: It involves verifying that users possess the necessary credentials and rights to access certain applications or data. Access management systems, such as Empower ID, streamline the process of handling access requests from end-users.
- Real-Time Verification: The access management process verifies user credentials at runtime. When users attempt to access a system or resource, their identity must be authenticated against the access policies established by the organization. If successfully authenticated, users are granted access based on their roles and permissions.
Access Request Handling
- Users can request access to specific applications or resources they need to perform their job functions. Access management tools facilitate this process, often employing workflows to route requests through the appropriate approval channels.
- The system can automatically alert approvers and track the approval process, ensuring that any access granted is compliant with organizational policies.
Governance in Access Management
Governance in access management defines how access rights are assigned, managed, and monitored. It not only governs who can access what but also establishes processes for how those rights are determined and modified.
Key Components of Governance:
-
Role Configuration: Governance begins with the initial configuration of roles within the system. An organization must define the access rights linked to each role, determining which groups, applications, and permissions should be included. This setup requires careful analysis and designation to ensure that roles provide appropriate access without unnecessary privileges.
-
Approval Processes: Once roles are established, there needs to be a governance process that dictates how access requests are granted. This includes the requirement for approvals before users can be added to specific roles or given particular access rights. Having a formal approval process helps ensure that access is managed responsibly and in line with company policy.
Access Governance Process
-
Role Management: As demands change, roles must be managed accordingly. If a role needs modification—either by adding or removing access rights—it should go through a structured governance process to assess risks and implications. This audit-like approach ensures that roles remain relevant and secure over time.
-
Access Certification: Regular reviews of user access rights are essential for compliance and security. Access governance includes a periodic examination of users’ access levels to verify that they still fit the defined criteria for their roles. This is often done through recertification processes whereby responsible parties are required to attest to the appropriateness of user access levels.
Importance of Access Management and Governance
Effective access management and governance are crucial for:
- Security: Minimizing the risk of unauthorized access or data breaches by ensuring that users only have access to the information necessary for their roles.
- Compliance: Upholding regulatory requirements related to data protection and access controls, thereby avoiding potential fines or penalties.
- Operational Efficiency: Streamlining processes to manage access requests and rights adjustments reduces delays and administrative overhead, allowing the organization to operate smoothly.
In summary, access management and governance work in tandem to create a controlled environment where user access is secure, compliant, and efficient. By implementing a structured governance framework, organizations can effectively manage how users interact with their digital resources, maintaining the integrity and security of their systems.
Single Sign-On (SSO) and Federation in IGA
Single Sign-On (SSO) and federation are essential concepts within Identity Governance and Administration (IGA) that enhance user experience and security by simplifying the authentication process across multiple applications and services. This section explores these concepts in detail, including their functions, benefits, and how they operate within an IGA framework.
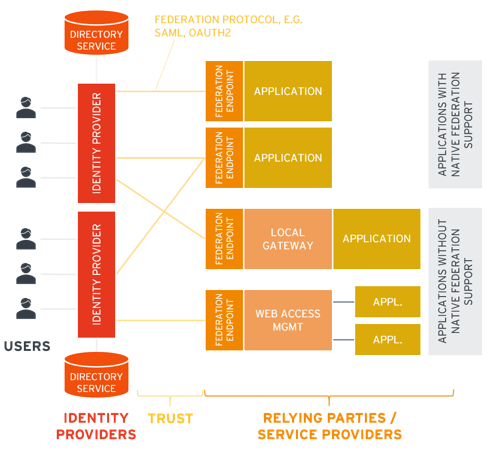
Single Sign-On (SSO)
Single Sign-On is an authentication method that enables users to access multiple applications and websites with just one set of credentials. This significantly reduces the need for multiple logins, improving user convenience and streamlining the login process.
Key Features of SSO:
- User Convenience: Users need to remember only one set of credentials, which not only saves time but also reduces the risk of password fatigue. This is particularly beneficial in organizations where employees access various applications daily.
- Secure Authentication: SSO enhances security by minimizing the number of times credentials are entered, thereby reducing the opportunities for credentials to be intercepted or compromised.
- Centralized Management: An SSO system centralizes authentication processes, enabling organizations to manage user access more effectively and enforce security policies across multiple platforms.
How SSO Works:
SSO operates through interactions between an Identity Provider (IdP) and Service Providers (SPs).
- User Initiation: The user attempts to access an application (the Service Provider).
- Redirect to IdP: If the user hasn’t yet authenticated, the SP redirects them to the IdP.
- Credential Verification: The IdP processes the user’s credentials (e.g., username and password) to verify their identity.
- Authentication Response: Once authenticated, the IdP sends a response back to the SP, confirming the user’s identity and granting access.
The user experience is seamless, as they do not need to log in separately to each application; instead, they are authenticated once by the IdP.
Federation
Federation refers to a trust relationship established between multiple identity and service providers that allows for the sharing of identity information across domains. This concept is crucial for enabling SSO across different organizations or systems.
Key Features of Federation:
- Trust Relationships: Federation creates a trusted connection between the IdP and SPs. When a user authenticates with the IdP, the IdP can assert their identity to multiple SPs without requiring re-authentication.
- Interoperability: Federation allows users from different organizations to access resources across organizational boundaries. For example, a partner company's employee can access the resources of another organization without needing separate credentials if appropriate federation agreements are in place.
- Enhanced Security and Control: By using federation, organizations can maintain control over their identity management practices while allowing users to authenticate using their existing credentials from a trusted IdP.
How Federation Works:
The process of federation typically involves the following steps:
- Establishment of Trust: Organizations must establish trust through agreements, which may involve exchanging metadata, certificates, and configuring systems to recognize each other.
- Identity Assertion: When a user authenticates with the IdP, the IdP provides a “token” or assertion of the user’s identity to the SP, which verifies the token before granting access.
- Access to Resources: The user can now access resources on the SP without needing to log in again, as the federation process handles the authentication.
SSO and Federation in Practice
Authentication Methods in SSO
When implementing SSO, various methods of authentication can be employed:
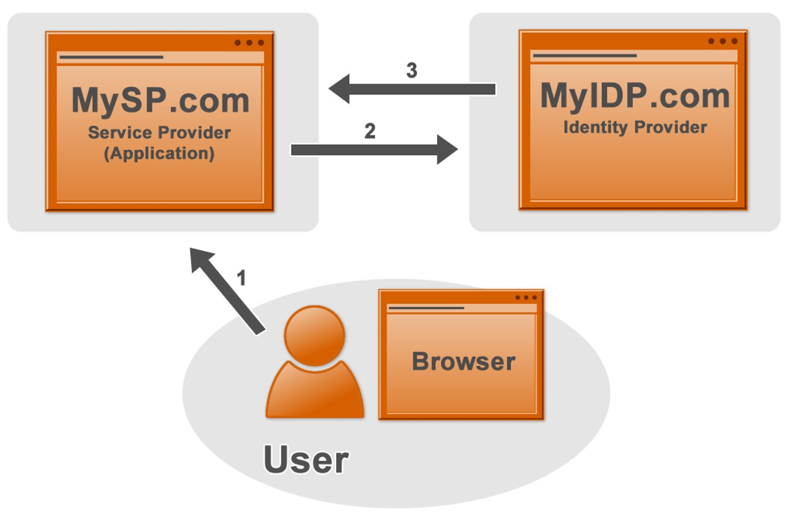
- Service Provider Initiated SSO: This involves the user accessing the SP directly. The SP recognizes the user is not authenticated and redirects them to the IdP for login. After successful authentication, the user is redirected back to the SP with their identity details.
- Identity Provider Initiated SSO: In this case, the user first logs into the IdP, which presents a dashboard of applications the user can access. Once the user selects an application, the IdP authenticates them with the SP.
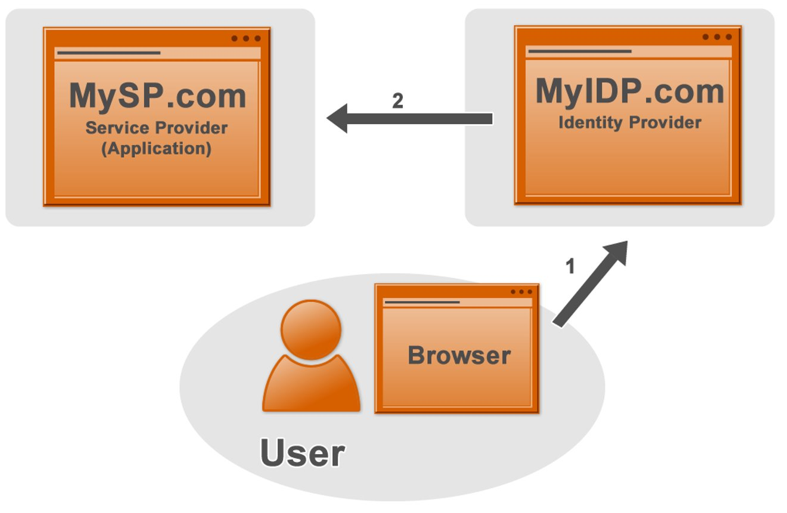
Authentication Flow
- Security Assertion Markup Language (SAML) and OpenID Connect are common protocols used in SSO and federation to facilitate secure exchanges of authentication and authorization data between the IdP and SPs.
Conclusion
Single Sign-On and federation play a critical role in modern IGA frameworks by enhancing user experience, improving security posture, and streamlining access management. Organizations that implement these technologies can offer their users a more convenient and efficient way to access a multitude of services while maintaining robust security controls and governance. Through SSO and federation, organizations not only simplify the authentication process but also establish a trusted ecosystem that promotes collaboration and connectivity across various platforms.
Compliance in IGA
Compliance is a critical aspect of Identity Governance and Administration (IGA), guiding organizations in adhering to regulatory frameworks and internal policies regarding data access and management. This section will elaborate on the importance of compliance within the context of identity management, the specific compliance requirements organizations face, and the processes involved in maintaining compliance.
Understanding Compliance
Compliance refers to an organization’s adherence to laws, regulations, and guidelines that govern how data should be managed, accessed, and protected. In the realm of identity management, compliance often manifests in relation to risk management and the verification of access permissions assigned to users.
Key Areas of Compliance:
-
Regulatory Compliance: Organizations must comply with a variety of regulations such as the General Data Protection Regulation (GDPR), Health Insurance Portability and Accountability Act (HIPAA), and others. Each of these regulations has specific requirements related to data security, user access, and accountability.
-
Internal Policies: Beyond regulatory needs, organizations establish internal policies to govern access and identity management. Compliance with these policies is essential for maintaining operational integrity and protecting sensitive data.
Risk Management in Compliance
In terms of identity management, compliance involves managing risks associated with user access and permissions. Organizations assess risks based on various access levels and need to align these with their risk tolerance and security policies.
Components of Risk Management:
-
Access Risk Assessment: Identifying and evaluating the risks associated with different access levels, which can vary from low-risk to high-risk data access. Certain data may necessitate stricter controls due to its sensitivity.
-
Segregation of Duties: Implementing segregation of duties to prevent any single individual from having access to both administrative and operational functions that could lead to fraud or unauthorized actions. This principle minimizes the risk of conflicts of interest.
Recertification Processes
Recertification is a critical compliance activity where organizations conduct periodic reviews of user access to ensure that permissions align with current roles and responsibilities.
Importance of Recertification:
-
Access Verification: Regularly reviewing who has access to specific resources ensures that only authorized users have ongoing access. If a user's role changes or they no longer require access, the permissions should be updated or revoked.
-
Audit Trails: Recertification processes generate audit trails that are essential for demonstrating compliance during regulatory audits. These records can show when access was granted, modified, or revoked, providing transparency and accountability.
Implementing Recertification:
-
Automated Tools: Many organizations leverage automated compliance tools that help manage the recertification process efficiently. These tools can prompt administrators or managers when it's time for reviews, making the process systematic and less prone to human error.
-
Reporting and Documentation: A clear documentation framework for the recertification process allows organizations to maintain compliance records needed for future audits, ensuring that all reviews and decisions are well-documented.
The Role of IGA in Compliance
IGA frameworks that incorporate compliance measures reduce the risk of data breaches, violations of regulations, and possible penalties. By establishing and enforcing policies for user access and identity management, organizations can:
-
Maintain Security Posture: Ensure that access rights are managed systematically in line with compliance requirements, enhancing the overall security posture of the organization.
-
Streamline Audits and Reporting: Improve the efficiency of the audit process by having a robust identity management system that clearly tracks access permissions and changes, making it easier to prepare for regulatory assessments.
-
Protect Sensitive Data: By enforcing compliance with access policies, organizations can better protect sensitive data from unauthorized access or breaches.
Conclusion
In conclusion, compliance within IGA is an essential aspect that requires careful attention and management. Organizations must navigate a complex landscape of regulatory requirements and internal policies while maintaining effective risk management practices. By integrating these compliance considerations into their identity governance frameworks, organizations can enhance security, support accountability, and ensure ongoing adherence to the rules and regulations that govern data access and identity management. By prioritizing compliance, organizations not only protect themselves from potential penalties but also foster trust with customers and stakeholders.
Roles-Based Access Control (RBAC) in IGA
Roles-Based Access Control (RBAC) is a foundational principle in Identity Governance and Administration (IGA) that enables organizations to efficiently manage access permissions across applications and protected resources. This section will explore the key components, benefits, and implementation strategies of RBAC within an IGA framework.
Understanding RBAC
RBAC is a framework designed to restrict system access to authorized users based on their roles within an organization. It recognizes that most users require access based on their job functions rather than individual needs, thus streamlining the management of permissions.
Key Features of RBAC:
-
Role Definition: Each role is defined according to the specific job functions within the organization. Common roles might include Analyst, Manager, Developer, CEO, etc. Each role encompasses a set of permissions corresponding to the tasks and responsibilities associated with that job title.
-
Contextual Access: RBAC also takes into account the context in which actions are performed. For example, a user’s access may depend not only on their role but also on their location or the department they belong to, ensuring that access rights reflect both job and situational context.
The Role Management Process
Role-Based Access Assignments
-
Birthright Access: Access rights are grouped into roles rather than assigned on a user-by-user basis. When a new employee joins the organization, they are assigned a role that automatically grants them the relevant permissions. This is referred to as “birthright access” because the access comes with the role they occupy.
-
Dynamic Management: As employees progress—through promotions, transfers, or role changes—their access rights can be adjusted seamlessly through their assigned roles, rather than needing to alter individual permissions.
Role Configuration
-
Role Creation: The first step is to create roles based on organizational needs. This involves understanding job functions and delineating access requirements for various positions within the organization. Careful consideration must be given to ensure that roles do not clash and that they maintain appropriate levels of access control.
-
Approval Process: Establishing an approval process for role creation and modification is essential. This ensures that only authorized personnel can create or adjust roles, maintaining tight control over access permissions.
Implementing RBAC
Automating Role Assignments
-
Integration with HR Systems: Many organizations use their Human Resources systems to automate user role assignments based on data such as department, job title, and employment status. This integration promotes efficiency and reduces administrative burdens.
-
Ongoing Role Management: The RBAC system should be regularly maintained to reflect changes in the organization, including updates to roles, permissions, and job functions. This maintenance might involve revisiting roles and ensuring they continue to meet business and security needs.
Monitoring and Auditing Roles
-
Security and Compliance: Regular audits of user roles and access rights are critical to ensure compliance with internal policies and external regulations. Organizations should have an established protocol to periodically review and certify that users are appropriately assigned roles based on their current responsibilities.
-
Revising Role Policies: As organizational structures change, role definitions may need to be adapted. A proactive approach to role management involves continually assessing and revising roles to maintain relevance and security.
Alternatives to RBAC
While RBAC is widely used, there are alternatives that may complement or offer additional flexibility:
-
Policy-Based Access Control (PBAC): This approach uses policies to determine access rather than fixed roles. It emphasizes attributes and contexts related to user and resource characteristics.
-
Attribute-Based Access Control (ABAC): ABAC extends the concept of RBAC by considering user attributes, resource attributes, and environmental conditions to make access decisions. This can add granularity but may also increase complexity.
Benefits of RBAC
Implementing RBAC in an organization offers several key advantages:
-
Efficiency: Simplifies the process of managing access rights. Instead of adjusting permissions for individual users, administrators can manage roles, making changes that automatically affect all users assigned to that role.
-
Enhanced Security: By providing access based on organizational roles, RBAC minimizes the risk of unauthorized access, as users are only granted permissions relevant to their job functions.
-
Streamlined Compliance: RBAC facilitates compliance with regulatory standards by providing clear documentation of access rights and policies related to user roles. This makes audits and compliance reporting significantly easier.
Conclusion
In conclusion, Roles-Based Access Control (RBAC) is a vital component of Identity Governance and Administration that allows organizations to efficiently manage access permissions aligned with job functions. By implementing a structured RBAC framework, organizations can not only enhance security and compliance but also promote operational efficiency and agility in their identity management practices. RBAC paves the way for organizations to adapt quickly to changes in personnel․․․
Privileged Access Management (PAM) in IGA
Privileged Access Management (PAM) is a crucial component of Identity Governance and Administration (IGA) that focuses on securing and managing access for accounts with elevated permissions. This section explores the key features, challenges, and best practices related to PAM within an IGA framework.
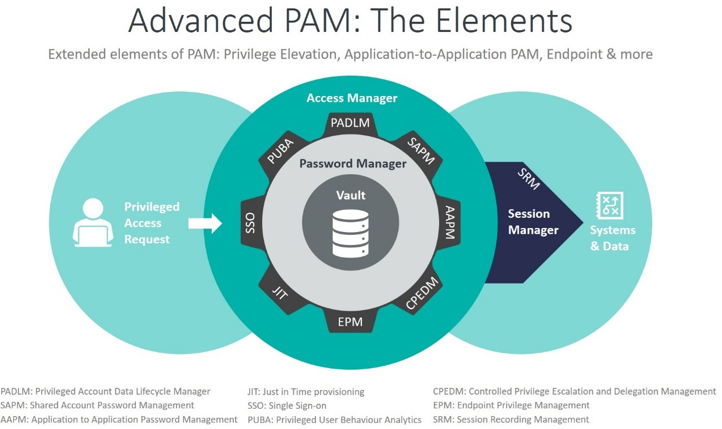
Understanding PAM
PAM is designed to control and monitor access to accounts and systems that are deemed critical due to their ability to grant broad access rights or administrative capabilities. Privileged accounts may belong to administrators, IT personnel, or any user who has elevated rights that can significantly impact the organization's security.
Key Features of PAM:
-
Credential Vaulting: One of the core features of PAM is the secure storage of privileged credentials. This vaulting mechanism protects these credentials from unauthorized access while ensuring they are readily available when needed.
-
Credential Rotation: PAM solutions often automate the rotation of these privileged credentials, which minimizes the risk of credentials being compromised or misused over time. Regular rotation also complies with best practices and regulatory requirements.
-
Session Management: PAM includes tools for managing and monitoring privileged sessions. This means that anytime a privileged account is used to access critical systems, the session can be logged, monitored, and potentially recorded for auditing purposes. By tracking these sessions, organizations can maintain oversight of activities conducted under privileged accounts.
Challenges in PAM
Implementing an effective PAM solution comes with its challenges:
-
Complex Environments: Many organizations operate in complex environments with numerous systems, applications, and cloud services. Coordinating PAM across these diverse platforms can be challenging and requires thoughtful planning and integration.
-
User Resistance: Employees may resist changes in how they access systems, especially when it involves more stringent controls or additional steps for authentication. Overcoming this resistance is critical for successful PAM implementation.
-
Balancing Security and Usability: While enforcing security controls is essential, organizations must also consider the usability of their systems. Striking a balance between strong security measures and user convenience can be difficult but is necessary to ensure compliance and ease of use.
Implementing PAM
Key Components of a PAM Solution:
Access Control Policies: Establish clear policies defining who can access privileged accounts and under what circumstances. Implement least privilege principles—granting users only the access necessary for their role.
Multi-Factor Authentication (MFA): Require MFA for accessing privileged accounts to ensure that even if a password is compromised, an additional layer of security is in place. This significantly enhances the security posture of both privileged accounts and the entire organization.
Audit and Compliance Reporting: Regularly audit privileged access logs and generate compliance reports. This visibility into privileged account usage can help detect unauthorized access attempts or suspicious activities.
Just-in-Time Privilege Elevation
-
One innovative approach utilized in many PAM solutions is Just-in-Time (JIT) privilege elevation. This strategy enables users to obtain elevated access temporarily for specific tasks, thus reducing the amount of time that high-level privileges are active.
-
Example Scenario: A developer may need administrative access to troubleshoot a server issue. With JIT elevation, they can temporarily gain these privileges, complete the required task, and then have those elevated permissions revoked automatically after the session ends. This minimizes unnecessary exposure and aligns with the principle of zero standing privileges.
Monitoring and Session Recording
Monitoring Privileged Sessions
- PAM solutions typically provide capabilities for monitoring user actions during privileged sessions. Organizations can observe real-time activities, which helps in identifying any unauthorized or unusual behaviors.
Session Recording
- Recording privileged sessions allows organizations to have a complete audit trail of actions taken during those sessions. This is particularly important for compliance needs, as it provides solid evidence of what actions privileged users performed and when.
Benefits of PAM
Implementing PAM in an organization provides numerous advantages:
-
Enhanced Security: By securing privileged accounts and controlling their use, organizations significantly reduce the risk of data breaches and unauthorized access to sensitive information.
-
Improved Compliance: PAM ensures that organizations can maintain compliance with relevant regulations and standards (such as GDPR and HIPAA) by demonstrating the secure handling of privileged access.
-
Increased Accountability: Through monitoring and session recording, organizations can hold users accountable for their actions. This fosters a culture of security awareness and responsible behavior regarding data access.
Conclusion
In conclusion, Privileged Access Management is a critical aspect of Identity Governance and Administration that focuses on securing and controlling access to privileged accounts. By implementing PAM effectively, organizations can enhance their security posture, streamline compliance processes, and manage risks associated with elevated privileges. With features such as credential vaulting, session monitoring, and just-in-time privilege elevation, PAM helps organizations mitigate the risks posed by privileged accounts while maintaining appropriate access for․․․